ITOM with ServiceNow
If you use Discovery or Orchestration with ServiceNow, you should probably follow this architecture.
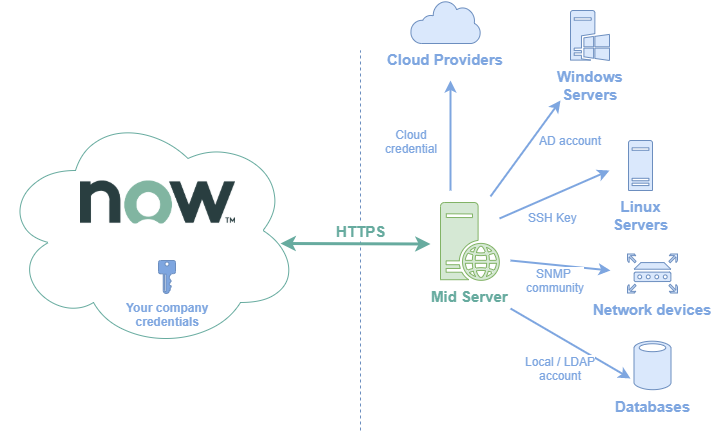
Your credentials used to connect to your systems are stored into the ServiceNow instance. When you schedule a Discovery, the credentials are send securely to the MID Server that uses them to connect to your systems.
Your credentials are crypted into the ServiceNow instance, but they can easily uncrypted if you have suffisant privileges.
Discover Windows Servers
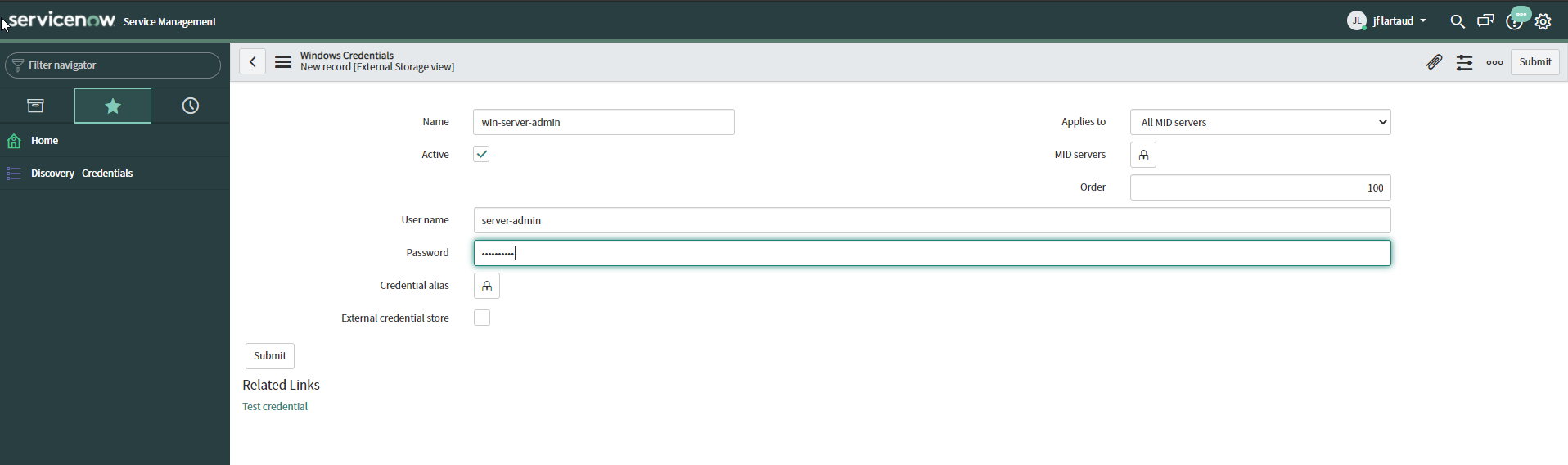
For example if you need to discover Windows Servers you have to create a Windows credential with an Admin Server account.
The screenshot below shows you how to create a Windows credential to discover Windows Servers from the Discovery > Credential menu. This is simple but not enough secure
Now imagine you have a secure secrets storage like Hashicorp Vault. Maybe it’s already the case into your company. In a few words this software manages your secrets. It is installed in your company’s information system. For our objective to discover Windows Server, it can store securely the Admin Server account password and even rotate it automatically.
To do this we need :
- an instance of Hashicorp Vault. Follow this tutorial if you want to begin with Hashicorp Vault
- an AD Account that have permissions to reset passwords (espacially on the Admin Server account)
- the External Credential Storage plugin activated into ServiceNow
- a connector to link ServiceNow and Hashicorp Vault: Vault-Connect
Our new architecture is the one describe below
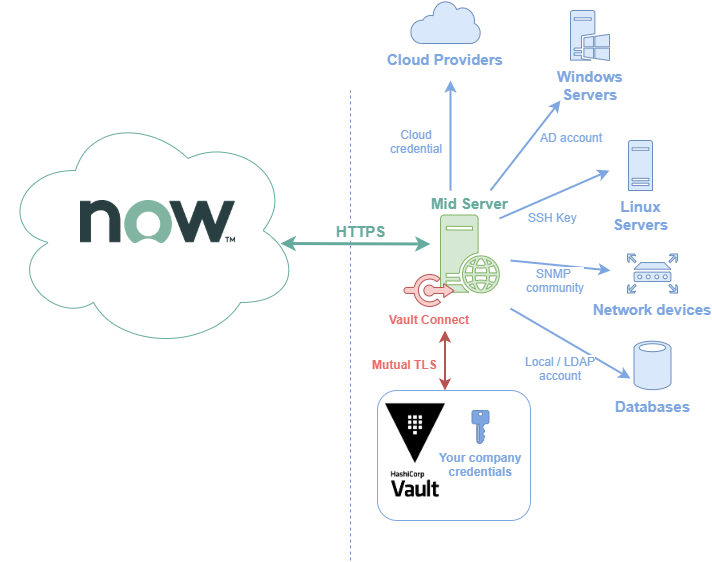
To secure our Admin Server account we need to follow a few steps